Enterprises continuously strive to engage in successful business partnerships with third-party companies and vendors to drive growth, expansion and also to speed up operations. This rapid growth strategy however exposes the company to growing risk of being breached by sometimes ‘unreliable third-party entities’. The continuous interactions and exchange of information that such arrangements entail open the possibility of potential data breaches thus putting the organization to great risk.
One of the critical measures that enterprises must necessitate within themselves at a nascent level is to have stringent metrics while considering engaging with a third-party vendor. Organizations must prioritize an effective third party risk management framework aka TPRM framework to mitigate undue risks and excessive costs incurred due to untoward incidents. While the relationships are important and critical for the businesses to thrive, yet the associated factors such as cyber risks, loss of reputation or even regulatory mishaps need to be factored with utmost priority. The answer therefore lies not in limiting engagement with third parties, but in ensuring effective management of third-party risks so that business is conducted with utmost trust and confidence.
As per a study by Markets and Markets, the size of the global Third-Party Risk management (TPRM) market is expected to grow from USD 3.2 billion in 2019 to USD 6.4 billion by 2024. The CAGR growth rate is 15.9% higher in the forecasted period. This is a clear indication that organizations dependent on third-party vendors are seriously considering the use of TPRM for their enterprises.
The purpose of this blog is to provide a foundational understanding of the Third-Party Risk Management (TPRM) realm and to emphasize the significance of selecting the right security expert to provide adequate measures. Let us begin with the fundamentals to get a comprehensive grasp of the subject in discussion.
What is TPRM?
Third Party Risk Management, also abbreviated as TPRM, is an ongoing process of discovering, assessing, and controlling third-party risks related to organization's data, their operations, financial information, or any type of confidential exchange.
Organizations collaborate with third-party vendors for two major reasons. The first is to support their business operations, and the second is to leverage additional benefits from these third-party vendors. This engagement massively contributes to reducing costs, focusing more on core business functions, and enabling best-in-class service from experts of relevant industries.
On the flipside, this kind of arrangement exposes organizations to unwanted data breaches along with cybersecurity & regulatory compliance risks that have the propensity to disrupt your business operations and damage reputation. Verifying third parties' reliability requires due diligence.
Gartner’s prediction concurs with the above sentiment. By 2025, 60% of organizations will use cybersecurity risk as a significant determinant in conducting third-party transactions and business engagements. This data insight is an eye opener to why one needs an TPRM program in the first place.
Now that the basis of the TPRM program is set, let us understand how a third-party risk management system works? What is the process and how does the typical workflow function?
Typical TPRM Workflow
To start with, organizations must identify all the vendors and begin categorizing them as per enterprise dependencies for sustainability and on the basis of critical business operations. Once you have identified the potential of the third party you want to associate with, start following these steps.
- Review contracts with complete due diligence.
- Identify the required people, process, and the technology controls to be adhered by the vendor.
- Perform a detailed third-party risk assessment (TPRA) to ensure that the underlying risks are mitigated and are within the acceptable risk levels.
- Ensure there is a remediation plan in place to timely mitigate vendor risks.
As an example, here is an illustration of a typical TPRM workflow we at InfoVision follow for our TPRM services:
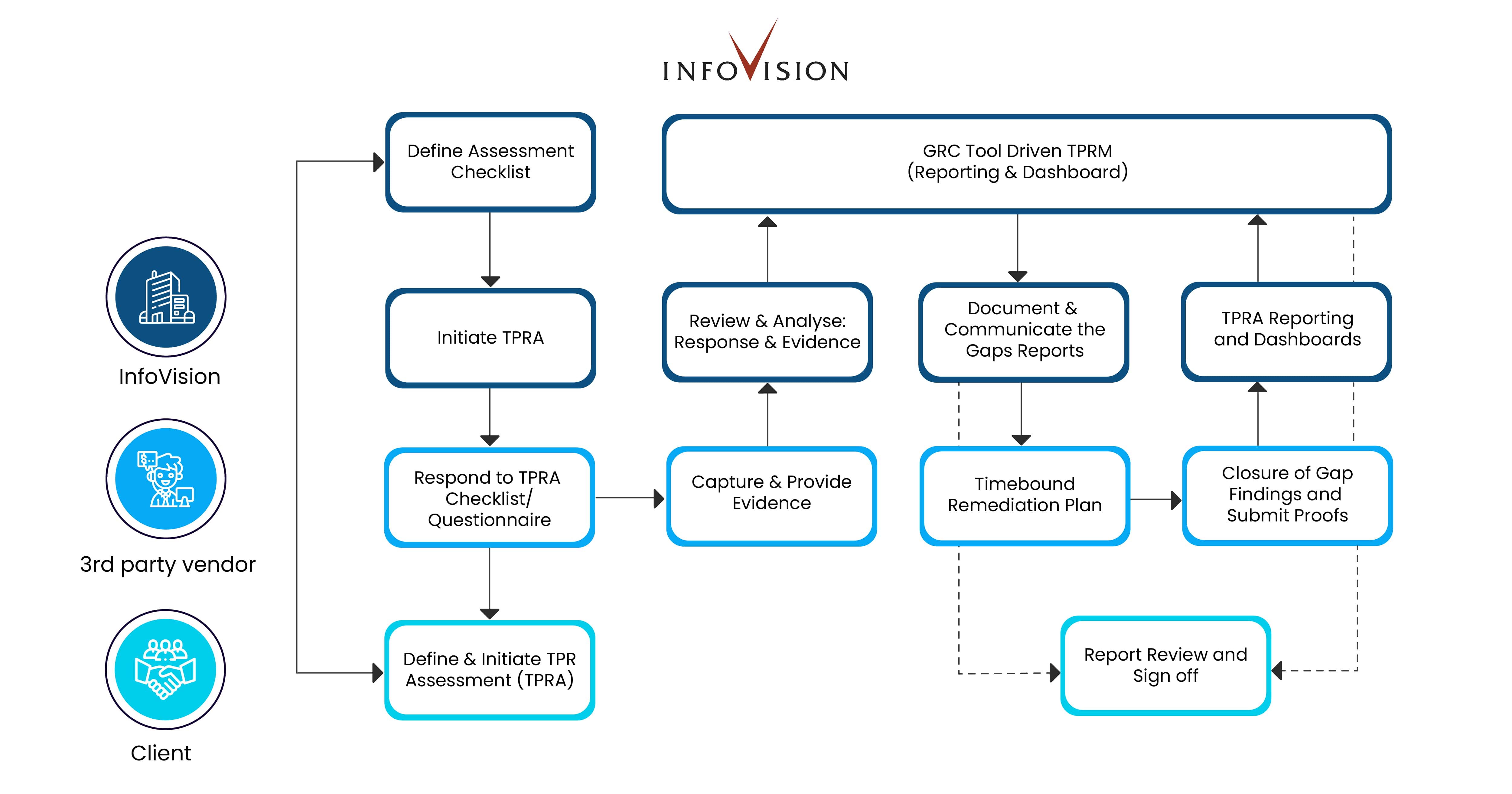
Devising a Cyber Due Diligence Plan: The InfoVision Way
It is a daunting task for enterprises to find the best and the right security experts for their TPRM initiative. Other than the process of finding the right fit, there are additional challenges such as,
- efficient fit-for-purpose process and procedures
- identification and mapping of various regulatory compliance/controls with respect to available vendors, and
- Automated TPRM programs
These are some of the major setbacks for security leaders. An effective TPRM program can improve overall visibility & results, easily validate, review third-party artifacts, take measures for potential risks and improve on efficiency.
InfoVision employs a distinctive strategy to strengthen its defense against potential hazards that may arise from third-party companies or vendors. This is achieved by thoroughly screening vendors through TPRA and selecting the appropriate ones. As the process progresses, all issues associated with third-party vendors are documented and evidence is collected. This evidence is then reviewed and analyzed, and a response is provided to the third-party provider, ensuring that they rectify the identified risks within the agreed-upon timeframe. The discrepancies are presented to our client's leadership in the form of reports and dashboards utilizing automated GRC tools.
Here are the distinguishing factors and added benefits of our TPRM program.:
- Customed dashboards and various compliance reporting templates help our client CISOs to take better informed decisions.
- A dedicated security advocate to assist client vendors in redefining their people, process, and technology controls to improve their compliance and security posture.
- Our approach optimizes the use of security experts and promotes left shifting by employing GRC tools for automation purposes.
- We create and implement a tailored TPRM program process, procedures, and framework that aligns with the unique needs of our clients.
In this way, InfoVision helps its clients to accelerate their Vendor Risk Management programs, thus limiting human errors, ensuring timely risk identification, providing for scalability with no additional resources, and improved governance & compliance.
How can a TPRM program be a game changer?
As per KPMG, Six out of ten people (61%) think TPRM is undervalued given its crucial function for the organization. Businesses might sustain greater expenditures and gain new efficiencies when it comes to resilient operations, cyber security and fraud detection if they have a strong TPRM program rather than just focusing on its individual components.
Additionally, leveraging automation through third-party risk management frameworks and technologies is a viable alternative when looking for ways to advance third-party security.
InfoVision is proficient with a dedicated team of specialized Enterprise Cybersecurity & Risk Services (ECRS) practitioners and experts who can help you with a ‘fit-to-purpose’ for your business. We can help your security leadership teams manage the TPRM program and devise your overall security strategy. Our unique approach leverages a blend of technology, industry experience, security domain expertise and fine-tuned processes to help you conduct your business with trust and confidence.
Raise your queries and speak to our specialists by writing to us at info.ecrs@infovision.com.

