In recent years, the landscape of cyber threats has dramatically transformed. As smart devices proliferate, the internet's expansion mimics a wildfire, perpetually serving as a fertile ground for emerging threats. Ransomware is indeed a major concern for organizations, especially smaller and less-protected ones, accounting for 72.7% of the cyberattacks in 2023. Trends indicate cyberattacks focusing on data theft and ‘extortion-only’ campaigns. For instance, the MOVEit or GoAnywhere attacks from 2023 refrained from using encryption-based ransomware, instead demanding extortion payments to prevent the disclosure of stolen data. According to Emisoft’s research, US-based organizations made up 83.9% of known MOVEit corporate victims, with Germany, Canada, and the United Kingdom following. Another notable instance of a ransomware attack was the breach that Hatch Bank experienced as a result of the GoAnywhere vulnerability. This served as a stark reminder of the real-world repercussions, affecting customer data and raising widespread concern.
Such examples highlight an evolving trend in cyberattacks, emphasizing the need for increased vigilance and robust cybersecurity transformation across all domains. ISG (Information Services Group) cybersecurity insights acknowledge that a significant portion of the SMB market is closely connected to large corporations, directly or indirectly, as part of a broader supply chain. Consequently, it is essential for SMBs to invest resources in implementing appropriate security measures to mitigate vulnerabilities, address control gaps, and establish robust policies.
Despite the trends, there is a noticeable difference in the approach and organizations’ investment levels within the market, reflecting the varying degrees of digital transformation between large and small organizations. Consequently, the method of identifying cybersecurity challenges and the subsequent efforts to establish a secure environment largely align with the digital maturity of the enterprise, regardless of its size.
Top challenges in addressing the complexities of cybersecurity

Businesses face critical challenges in recognizing threats originating from unprotected devices and endpoints, vulnerabilities in applications and software, cloud misconfigurations, legacy infrastructure, and internal risks. The costs of data breaches are rising steadily due to missed opportunities, regulatory fines, and investigations. For instance, healthcare breaches averaged nearly $11 million in early 2023, up 8% from the previous year. Cybercriminals target weak links in supply chains, expecting software supply chain cybersecurity attacks to compromise identities and data.
Organizations need to move beyond perimeter security to ensure partners meet security standards. Open-source software and cloud adoption introduce new risks, with threat actors exploiting vulnerabilities. Furthermore, digital transformation investments increase vulnerabilities, with over $10.54 million IoT security risks reported in December 2022 alone. Complying with government regulations and sanctions is a challenge by itself, which requires maintaining compliance with often complex and evolving standards, potentially resulting in increased operational costs and limitations on business operations to avoid penalties. For example, the US Securities and Exchange Commission (SEC) introduced a cybersecurity strategy in 2023, which underscores the recognition among C-level executives of the importance of security risks and the need for enhanced transparency in addressing breaches and threats.
The growth of technology also presents challenges for cybersecurity professionals and contributes to high employee attrition. Investments in digital technologies like IoT, AI, and ML have introduced increased, often unnoticed vulnerabilities in recent years. IoT adoption has expanded endpoints, leading to visibility challenges and susceptibility to attacks due to non-standard protocols and limited security integration. Furthermore, IoT invites concerns such as open source software, unpatched vulnerabilities, APIs, and weak password protection. This proliferation not only facilitates large-scale DDoS (Distributed Denial of Service) attacks but also heightens risks to critical infrastructure, with potentially severe financial and socio-economic consequences. Other trends, such as investments in remote work infrastructure, expand the enterprise perimeter and limit visibility across devices and applications, adding complexity to security efforts.
Many organizations also face challenges in aligning their CISO’s (Chief Information Security Officers) strategic security planning with overall organizational goals. ISG has identified specific hurdles, such as budget constraints, exacerbated by recession fears, that limit defenses against increasing cyber threats. Many CISOs struggle to allocate sufficient funds for effective security solutions and cybersecurity talent gap solutions. Lastly, operational challenges like work overload from alerts and technologies, complicated management by legacy systems, cloud misconfigurations, or the overarching need to adapt to emerging threats often overwhelm security teams.
How can organizations limit the attack surface?

Organizations that have robust cybersecurity measures prioritize business resilience in cybersecurity to withstand threats while maintaining trust, accountability, and customer experience. They invest in identifying and addressing vulnerabilities tailored to industry-specific risks. Key strategies include adopting the Zero Trust Security framework, SASE (Secure Access Service Edge), conducting rigorous risk assessments, and engaging in continuous monitoring, penetration testing, and red team simulations.
Suggested Read: The zero trust model: “trust no one” approach to cybersecurity
The “never trust, always verify” principle within the framework addresses various aspects such as perimeter-less enterprises, mutual authentication, explicit scrutiny, continuous monitoring, and network micro-segmentation. Implementing this framework necessitates a deep understanding of current security solutions and phased investments to consistently deploy relevant security measures tailored to the organization’s needs. Stricter vendor assessments and proactive prevention efforts complement robust response and recovery plans. Enterprises aim to conduct ongoing risk assessments and periodic audits across various domains, encompassing changes in business strategy, supply chain, M&A, and financial exposure. Additionally, resources are allocated to regularly conduct vulnerability scans and penetration tests to uncover insecure access points that may elude security analysts’ detection. CISOs collaborate with providers equipped with red teams to simulate advanced cyberattacks, gaining insights into vulnerabilities, weak access points, and potential pathways for adversaries to exploit sensitive data or disrupt networks. By addressing compliance, user experience, employee well-being, and customer assurance, innovative, user-oriented training supports employee awareness training in fostering a cybersecurity-centric culture.
Suggested Read: Red teaming: The future of cybersecurity preparedness
CISOs must prioritize solutions aligning cybersecurity transformation efforts with enterprise objectives, educating on cybersecurity risk management for resilience. Investments must be made to target specific industry threats, simplifying tools, and leveraging integrated suites for tailored risk management. Adopting automation and AI can greatly enhance threat detection, while managed services can address talent shortages. Prioritizing integration with existing tools or suites featuring extended detection and response capabilities will ensure smooth operations.
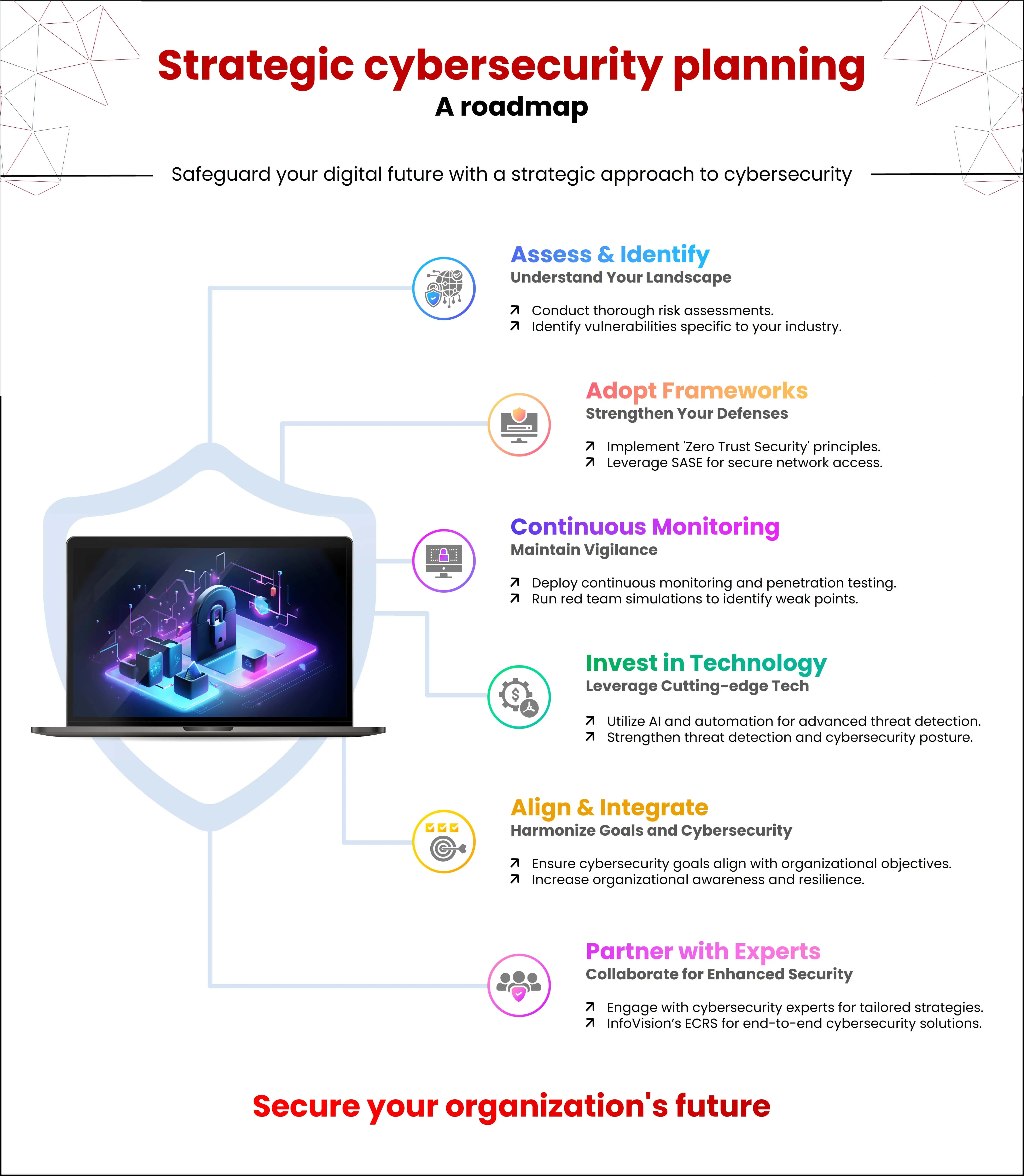
Partnering with domain experts like InfoVision enables businesses to seamlessly build robust cybersecurity strategies tailored to their business needs. InfoVision’s Enterprise Cybersecurity and Risk Services (ECRS) is a specialized cybersecurity practice that enables our customers to address their cybersecurity issues and enhance their cybersecurity transformation posture. The ECRS encompasses various capabilities, including GRC (Governance, Risk, and Compliance), SVS (Security Vulnerability Scanning), ISS (Integrated Security System), and IAM (Identity and Access Management) with Cross-Skilled Resources.
Cybersecurity transformations require rigorous efforts
As the cybersecurity transformation progresses, it’s imperative for businesses to remain adaptive and proactive in safeguarding digital assets and maintaining a resilient security posture. By staying ahead of emerging threats and continuously refining their security strategies, they can effectively mitigate risks and protect against potential breaches. With the ever-changing nature of cyber threats, a proactive stance is essential to ensuring the long-term security and stability of enterprise systems and data.
Looking to bolster your cybersecurity infrastructure? Make the most of our cybersecurity solutions and embrace digital security change with confidence.

